
There is a shift to digital platforms in today’s modern era. Various accounts and sites require that you provide your credentials such as identity number, your name, and other verification documents. To secure such vital information in the various sites, there is a need to secure with strong passwords.
A strong password is not enough to make your website immune from being by-passed by unauthorized third parties. The following methods will help to ensure your online data is secure, and only authorized users can access such vital information.
Password manager
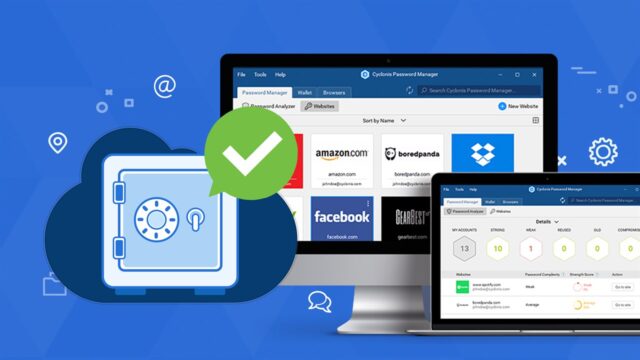
A password manager is a program that stores all the computer passwords in the cloud, computer, or encrypted vault and you can click here for more details. You, as the user of the system, can access the passwords with a master password. The use of password managers is one of the safest methods to keep track of your various passwords. The use of this software allows you to use stronger and lengthy passwords without the need to remember them.
In the process of logging into a site where you haven’t saved the password before, the password manager will enable you to save it automatically in the vault and you can access it in the future. Also, if you change a password in a specific site, the password manager will automatically replace the old password with a new password in the encrypted vault.
Password managers are also useful in organizations where several employees need to gain access to a particular website. The passwords can be saved in the cloud where all employees can access them. You can create a master password and give it to the employees which they will use to gain access to the rest of the passwords. The method ensures seamless access to various sites and prevents people who don’t have the authorization from obtaining the company’s important data.
Two-factor authentication
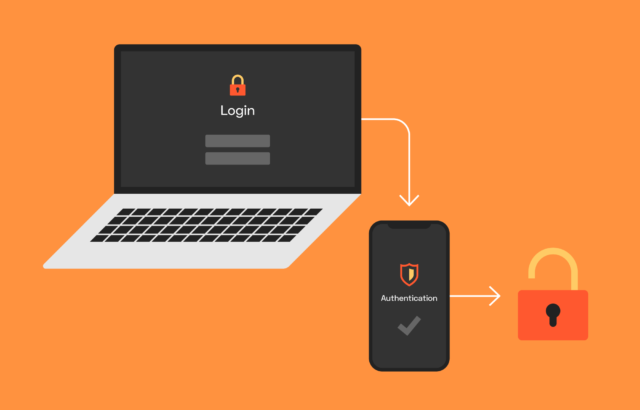
The two-factor authentication is also referred to as dual-factor authentication or two-step verification. The verification process requires users of the account or sites to identify themselves using a second method after keying in the password. The sites can direct you to enter special codes sent through a text message to your phone.
The verification process adds an extra layer of robust security by requesting you for a second factor. The process is better than the single-factor authentication (SFA) that relies on a single element. Depending on the logging site you might require to verify your identity when you use a new device to log in to your account.
They are numerous verification factors that sites which include:
- Knowledge factor-is something that you are familiar with, such as a password, secret phrases, or personal identification number.
- Possession factor-something that you own, such as an identity card number, mobile device, or security token.
- Inherence factor- also referred to as a biometric factor. They are credentials that are particulate to you such as fingerprints, facial recognition, or voice recognition.
- The location factor-it mainly tracks the physical geographical location of the device being used for logging into the account. The method uses Internet Protocol (IP) or Global Positioning System (GPS) to locate the location of the user of the account.
- Time factor-some accounts or sites have a specific time duration or window where you are permitted to access. The sites restrict accessing of the system outside the given time frame.
Software updates and patches
The software update is the process of making changes to an app such as bug fixes, updating the hardware, or some minor security patches. At the same time, patches involve addressing the security vulnerabilities within software or program. The process makes fixes that ensure your device has sturdy security features.
Older versions of software have many vulnerabilities, and hackers can gain access to the accounts or sites. New versions with new updates or patches are hard to hack as the fraudsters might not be in a position to exploit the latest software.
Unique password for each site

Each account needs to have a unique password that is difficult to crack. Creating unique passwords for each site is useful; if you want to change a password on one account, you don’t need to change the other accounts. A password manager helps in the saving of numerous passwords from different accounts.
Even if you have a strong password reusing it puts the accounts at risk. If you happen to log in to an unsecured website a hacker can easily gain access to your login credentials and hack some of your accounts. If you happen to use the same passwords for numerous accounts, the hackers can access multiple accounts in your name and use that information for fraudulent activities.
Secure websites

Web security is essential in keeping fraudsters and hackers from accessing sensitive information. Unsecure sites escalate the chances of malware, cyberattacks, and attacks on websites. Generally, sites that are secure user authentication and encryption to ensure user’s confidentiality.
HTTPS offers robust security and protects the users of various websites from hacking activities. Most of these cyber attacks are made through insecure networks, and hackers can access your important documents and information. The HTTPS ensures that any communication between websites is secure and encrypted.
The main advantages of using HTTPS to secure websites include

- Data encryption-data in the HTTPS is encrypted, which prevents any unauthorized persons from accessing the information. Even though the hacker obtains the data, they can’t translate it to something meaningful as it’s encrypted using a certain code.
- Data protection-HTTPS does not save information on the system. If you login to your credentials in a public network, the HTTPS will not save that data, thus enhancing robust data protection.
- Authentication-the HTTPS ensures that you don’t provide your critical data to invalided servers. It allows you to leave an unsafe site in time by providing various warnings.
Bottom Line
Your credentials can be used by fraudsters to route money from your account, conduct fraudulent activities, impersonification, among other illegal activities. Most sites don’t offer 100% security of data from hackers, and you need to be coherent enough to adopt the right strategies. Password managers, two-factor authentication, software updates and hatches, unique passwords for each site, and secure websites are the best strategies to keep your online data safe.






